The Heart of Secure Communication: Cryptography and Digital Trust
This article explores the core principles of secure communication, focusing on symmetric and asymmetric cryptography, digital signatures, and digital certificates. It explains how these technologies work together to ensure data confidentiality, integrity, and authenticity in the digital world.
In today’s digital age, secure communication is not just a luxury, it’s a necessity. At the core of this security lies cryptography. This write-up explores the essential concepts and techniques that make secure communication possible, focusing on symmetric and asymmetric cryptography, digital signatures, and digital certificates.
The Building Blocks of Cryptography
Before diving into the main topics, it’s important to understand a few basic concepts that are prerequisites for better understanding.
Encryption and Decryption
Encryption is the process of converting plain text into a coded form, known as ciphertext, to prevent unauthorized access. Decryption is the reverse process turning the ciphertext back into readable plain text. Together they ensure that only the intended recipient can understand the message.
Key and Algorithm
In cryptography, a key is a piece of information used in conjunction with an algorithm to perform encryption and decryption. The algorithm is the set of rules or mathematical steps used to convert the plain text into ciphertext and vice versa. The security of encrypted data depends heavily on the secrecy and complexity of the key.
Hash
A hash function takes an input (or message) and returns a fixed-size output(string of bytes). The output is known as the hash value which is unique to the input. Even the slightest change in the input will produce a drastically different hash. Hashing is primarily used for verifying data integrity.
If you are familiar with the above concepts then it will be easy to understand the following main topics of this write-up.
Symmetric Key Cryptography
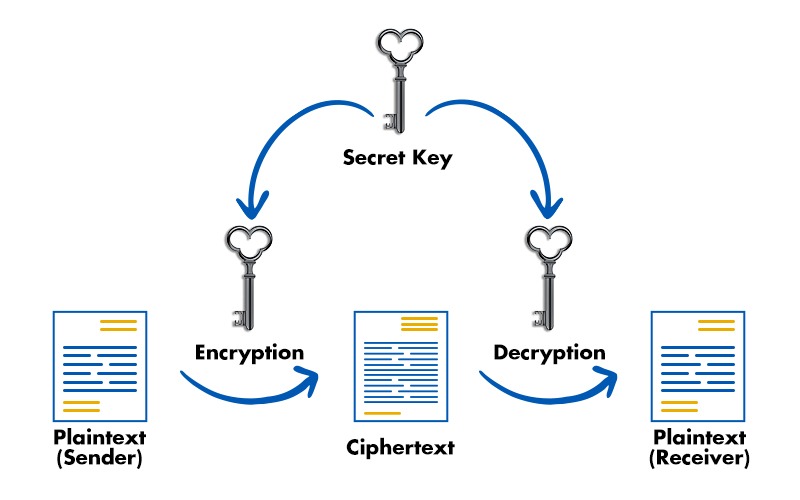
Symmetric key cryptography also known as private key cryptography is one of the oldest and most straightforward methods of encryption. In this approach, a single key is used for both encryption and decryption. However, there’s a problem here — can you guess what it is? Yes, the key must also be sent over the network. If an attacker can intercept the message between two parties then they can also intercept the key, making the encryption useless!
Symmetric Key Cryptography (From PyNet Labs)
Asymmetric Key Cryptography
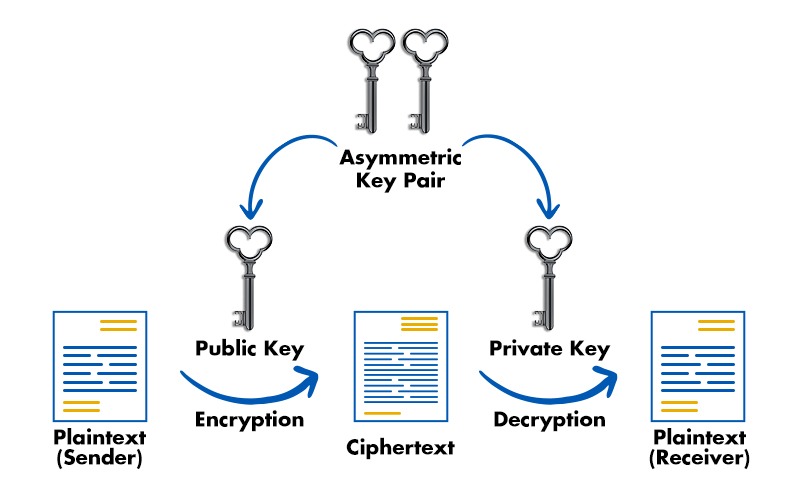
To overcome the key distribution problem in symmetric cryptography, asymmetric cryptography, also known as public-key cryptography, comes into play. This method uses two keys: a public key and a private key.
As the name suggests the public key is openly shared and anyone who wants to communicate with the key’s owner can have it. The private key, on the other hand is kept highly confidential. Here’s how it works:
- If you encrypt data with a public key then only the corresponding private key can decrypt it which ensures confidentiality.
- Conversely, if you encrypt data with a private key then it can only be decrypted with the corresponding public key which ensures data integrity and authenticity.
A typical flow looks like this:
User A will take the public key of User B, encrypt the data, and send it over. User B will then decrypt it using their private key. But there’s a problem here as well — can you guess what it is?
How can User A verify that the public key they received actually belongs to User B and not an attacker? If an attacker can replace User B’s public key with their own, they can intercept and decrypt the data intended for User B. This is where digital signatures and digital certificates come into play.
Asymmetric Key Cryptography (From PyNet Labs)
Digital Signatures
To solve the problem of verifying the public key’s authenticity, we use digital certificates and digital signatures. The basic idea is to prove the identity of the key owner. Remember, we saw earlier that the public key is distributed openly, but the private key is kept secret. So we can consider private key as identity of that user.
Here’s how it works:
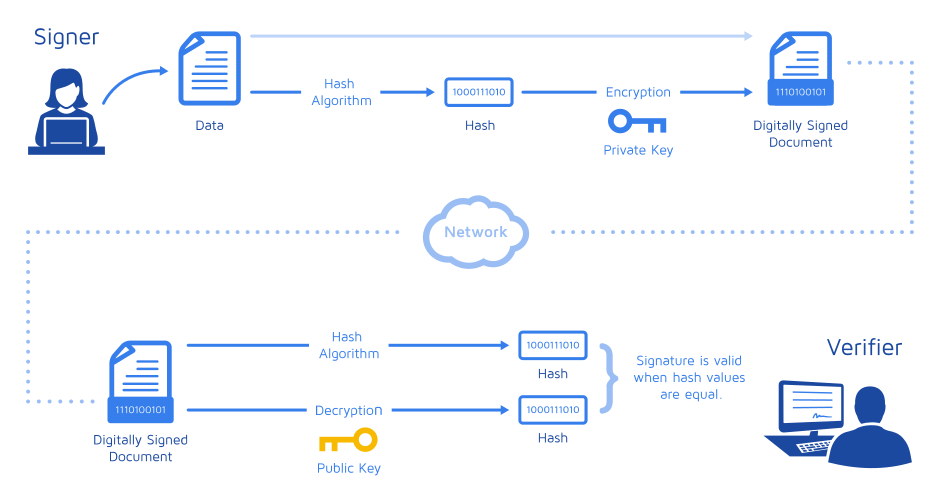
User B will create a hash of the data. This hash is then encrypted using User B’s private key, and the data, along with the encrypted hash is sent to User A. This encrypted hash is known as Digital Signature.
User A will decrypt the digital signature using User B’s public key and then hash the received data using the same algorithm. If the hash from the digital signature matches the hash from the received data then it means the data is authentic and hasn’t been tampered with.
In short a digital signature is used to validate the integrity of the data.
Digital Signature Workflow (From Docusign)
Digital Certificates
To further ensure the integrity of public keys and to confirm their ownership, we have digital certificates. A digital certificate acts like an ID card for the public key, validating who the public key actually belongs to.
How It Works:
- Certificate Authority (CA): A trusted organization called a Certificate Authority (CA) checks User B’s identity thoroughly.
- Issuing the Certificate: Once the CA is sure about User B’s identity, it issues a digital certificate. This certificate contains User B’s public key and other information, all digitally signed by the CA.
- Verification by User A: When User A receives the public key (in the form of a digital certificate), they check the CA’s digital signature on the certificate. If the certificate is valid, it confirms that the public key indeed belongs to User B.
Digital Certificate Workflow (From Internet)
Real-World Application
In the real world, asymmetric cryptography is resource-intensive, whereas symmetric cryptography is fast. To balance security and performance, asymmetric cryptography is often used to securely exchange a key for symmetric cryptography, which is then used for ongoing communication.
For instance, when you visit a website, the site sends its digital certificate to your browser. Your browser checks the certificate’s validity by verifying the CA’s digital signature using the CA’s public key, which is widely trusted and pre-installed in browsers. If the certificate is valid, your browser uses the website’s public key (from the certificate) to establish a secure, encrypted connection.
Final Thoughts
Cryptography, along with digital signatures and certificates, is the cornerstone of secure communication in the digital world. By ensuring that our data remains confidential, authentic, and tamper-proof, these technologies allow us to navigate the internet with confidence.
I hope you found this write-up insightful! If you did, please share it with your friends and colleagues. If you have any doubts feel free to ask. Don’t forget to follow Security Mates for more in-depth explorations of cybersecurity related topics.